

The Igaware Universal Threat Management (UTM) system protects your data and IT systems from all types of malicious attacks; Hacking, Denial of Service, Ransomware, Viruses, Phishing, Spam and more, with the major advantage that it is continuously updated against new and emerging threats
The Igaware UTM is included as part of the Igaware Linux Small Business Server but can be installed seperately to protect existing servers and data.
The Igaware UTM is Payment Card Industry (PCI) compliant giving you the highest possible level of security.
A firewall acts as a border control, preventing unauthorised access to your systems and data. Any network traffic attempting to enter or leave your network is either blocked or allowed according to rules or access policies. Rules block unauthorised access to your data and systems, and control what computers and devices on your network can access on the Internet.
A computer can be given, for example, an access policy of ‘Web Only’. This means the computer can’t access ftp servers and download malicious software, neither can it send and receive email from a third-party email server – it can only access email that has come via the Igaware UTM that has been securely filtered by the Igaware Email Filtering (see below).
To allow safe web browsing the Igaware UTM includes Web Filtering (see below).
Opening selected ports on the firewall can allow secure remote access to systems. For example, incoming email can be delivered through port 25. Inbound email is filtered for spam and malicious content before being safely delivered to recipients.
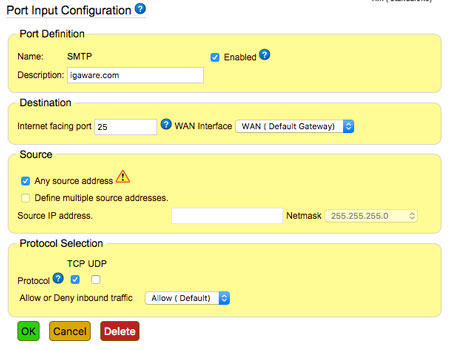
You can access data and email when you are away from the office using SSL (Secure Sockets Layer) VPN (Virtual Private Networking) ; the industry standard cryptographic protocol providing security over Internet. You can securely access your data and email via your laptop, mobile and tablet devices.
Remote offices and computers can be also be joined to your office network using secure IPSec and SSL VPN connections.
Hacking scripts are often run against network services in an attempt to gain access to a system. These can, for example, take the form of "brute force" attempts to guess a username and password for a service, such as SMTP AUTH, IMAP, etc. These scripts run un-attended for hours or weeks at a time. So, it's very important to protect against them.
The Igaware UTM detects network intrusion attempts and blocks the assailant from further access to the network service. If the assailant continues to attack the Igaware Firewall then they are blocked from accessing all network services.
Igaware Web Filtering prevents dangerous content, such as malicious software, from being accessed and downloaded from the web.
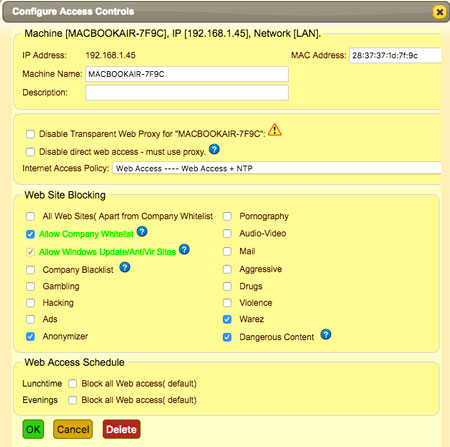
Internet usage can be monitored via reports showing web access, and you can control access to types of websites that you may deem unsuitable and unproductive for staff at work. You can stop staff hogging your network bandwidth by downloading and streaming video and music, for example, and ensure adult content doesn’t end up on your network.
Email is the preferred route for delivering malicious software. Hackers have become highly skilled at creating emails that look legitimate. tricking recipients into opening malicious attachments or following a link to a forged website and handing over user names and passwords. These types of scam emails are known as Phishing Emails. The Igaware Email Filtering has advanced anti-phishing defences, spotting fraudulent links, forged sender addresses and dangerous attachments.
Igaware Email Filtering will block all types of dangerous email content including; viruses, html scripts, forged links, password protected zip files and phishing.
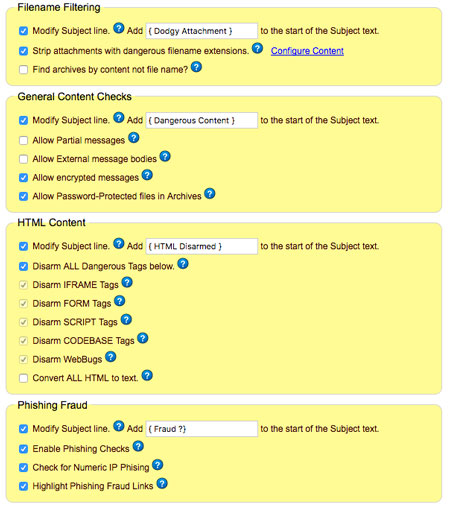
Igaware Email filtering includes comprehensive Anti-Spam Filtering keeping your inbox free from junk emails. Igaware Anti-Spam capabilities are very advanced and extensively covered in our Anti-Spam Guide.
Igaware uses a combination of open source software.
Open source software uses the principle of openness - code is visible to all making it easier to identify and plug security vulnerabilities faster.
Proprietary software such as Microsoft uses security through obscurity.
Security Through Obscurity is the idea that by hiding your software code no-one can find holes in it. It’s akin to burying your money under a tree. The only thing that makes it safe is no one knows it’s there. Real security is putting it behind a lock or combination, say in a safe. You can put the safe on the street corner because what makes it secure is that no one can get inside it but you.
The weakness of security through obscurity hit the headlines in 2017 as Windows software was hit by worldwide ransomware attacks following the leak of known software vulnerabilities from the NSA (US Government - they found Microsoft’s tree!) - https://www.theregister.co.uk/2017/04/14/latest_shadow_brokers_data_dump/
Igaware software is security hardened and unhacked in over 20 years.
Igaware Servers include options to backup your data locally and remotely. Backups are essential as servers can be stolen, destroyed by fire, deleted and corrupted.
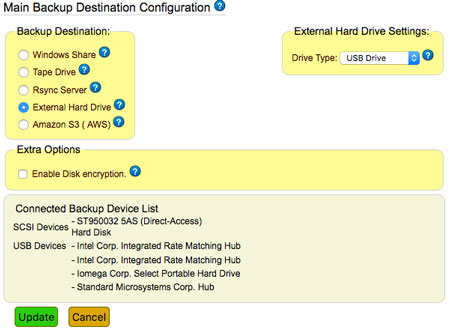
To keep your data safe Igaware servers have mirrored drives (RAID) to prevent service interuption in the event of a disk 'going bad'. Built in hardware monitoring means pre-fail warnings allow disk replacement before any serious failure. And if a server should 'die' disks can be swapped into a replacement server in a matter of minutes. We will supply replacement hardware as part of our support package.
If you have an office the sensible and secure place to have your data is next to you. You can control exactly who has access to it, ensure it is backed up, and access is maintained if the Internet fails.
Other vendors are pushing customers to the cloud, not because it is practical or secure for their customers but because it gives them complete control over your data - they can even read it! We have covered this subject in our blog -The Cloud – a reality check
If you use cloud services you still need an Igaware UTM to secure local data and infrastructure, and maintain control over Internet use.
If your data is of a highly sensitive nature, perhaps you hold personal financial data or work on MOD projects, then you can opt to have the Igaware file server and data backups encrypted. This ensures that if server or backup hard drives are stolen, data cannot be accessed.
Igaware software is constantly updated, this is what makes Igaware different; the whole software bundle, including the operating system and all applications, are constantly updated.
Support is also unrivalled. If for example you were having problems with remote access to data we can run in-depth network diagnostics to see where bottle necks are; there might be a faulty switch, a firmware issue with your router or a fault with you broadband. We can deliver the evidence to help you resolve these issues with your suppliers. This type of support in invaluable when things aren’t working. We don’t hand out support tickets, we get on with resolving issues.
Learn more about threats and the steps you can take to keep your data safe - Don't Get Held to Ransom -Keep your data safe and secure
To learn more about the Igaware UTM call us on 0191 303 6177.